Additionally, SQL injection is very common with PHP and ASP applications due to the prevalence of older functional interfaces. J2EE and ASP.NET applications are less likely to have easily exploited SQL injections because of the nature of the programmatic interfaces available.
A cross-site scripting attack sends malicious scripts into content from reliable websites. Find the right plan for you and your organization. In addition, A could also modify the message before resending it to P. As you can see, P is using encryption and thinks that his information is protected but it is not, because of the MitM attack.
While there are thousands of known variants of cyber attacks, here are a few of the most common attacks experienced by organizations every day. The malware landscape evolves very quickly, but the most prevalent forms of malware are: Denial-of-service (DoS) attacks overwhelm the target system so it cannot respond to legitimate requests.  Rootkits are installed inside legitimate software, where they can gain remote control and administration-level access over a system. A short time after the attack, press reports said 800-1500 small to mid-sized companies were infected by REvil ransomware as a result of the attack. Two weeks after the events, the US Justice Department charged three suspects, one of whom was 17 years old at the time. The updates were then distributed to SolarWinds customers. The WannaCry ransomware attack affected more than 300,000 computers in 150 countries, causing billions of dollars in damages. A cyber attack is a set of actions performed by threat actors, who try to gain unauthorized access, steal data or cause damage to computers, computer networks, or other computing systems. The attackers computer continues dialog with the server and the server believes it is still communicating with the client. This script might install malware directly onto the computer of someone who visits the site, or it might re-direct the victim to a site controlled by the hackers. P2 sends the encrypted symmetric key to P. P2 computes a hash function of the message and digitally signs it. Impervas solution enables cloud-managed services users to rapidly gain visibility and control of cloud data. QBot, also known as Qakbot, QBot, QuackBot, and Pinkslipbot, is a Banking Trojan that was first observed in 2007. Gain seamless visibility and control over bot traffic to stop online fraud through account takeover or competitive price scraping. The interconnectedness of things makes it possible for attackers to breach an entry point and use it as a gate to exploit other devices in the network. The global cost of cyber attacks is expected to grow by 15% per year and is expected to reach over $10 trillion. Fileless malware attacks can be triggered by user-initiated actions, or may be triggered with no user action, by exploiting operating system vulnerabilities. Increase the size of the connection queue and decrease the timeout on open connections.
Rootkits are installed inside legitimate software, where they can gain remote control and administration-level access over a system. A short time after the attack, press reports said 800-1500 small to mid-sized companies were infected by REvil ransomware as a result of the attack. Two weeks after the events, the US Justice Department charged three suspects, one of whom was 17 years old at the time. The updates were then distributed to SolarWinds customers. The WannaCry ransomware attack affected more than 300,000 computers in 150 countries, causing billions of dollars in damages. A cyber attack is a set of actions performed by threat actors, who try to gain unauthorized access, steal data or cause damage to computers, computer networks, or other computing systems. The attackers computer continues dialog with the server and the server believes it is still communicating with the client. This script might install malware directly onto the computer of someone who visits the site, or it might re-direct the victim to a site controlled by the hackers. P2 sends the encrypted symmetric key to P. P2 computes a hash function of the message and digitally signs it. Impervas solution enables cloud-managed services users to rapidly gain visibility and control of cloud data. QBot, also known as Qakbot, QBot, QuackBot, and Pinkslipbot, is a Banking Trojan that was first observed in 2007. Gain seamless visibility and control over bot traffic to stop online fraud through account takeover or competitive price scraping. The interconnectedness of things makes it possible for attackers to breach an entry point and use it as a gate to exploit other devices in the network. The global cost of cyber attacks is expected to grow by 15% per year and is expected to reach over $10 trillion. Fileless malware attacks can be triggered by user-initiated actions, or may be triggered with no user action, by exploiting operating system vulnerabilities. Increase the size of the connection queue and decrease the timeout on open connections.
Cyber attacks are increasingly common, and some of the more advancedattacks can be launched without human intervention with the advent of network-based ransomware worms. Social engineering is an attack vector that relies heavily on human interaction, used in over 90% of cyberattacks.
By accessing a persons password, an attacker can gain entry to confidential or critical data and systems, including the ability to manipulate and control said data/systems. Spear phishing is a very targeted type of phishing activity. P is also able to prove to himself that P2 was the sender because only P2 can sign the hash so that it is verified with P2 public key. Securing APIs requires a variety of measures, including strong multi factor authentication (MFA), secure use of authentication tokens, encryption of data in transit, and sanitization of user inputs to prevent injection attacks. Malicious actors often look for ransom or other kinds of economic gain, but attacks can be perpetrated with an array of motives, including political activism purposes. This causes the target system to time out while waiting for the response from the attackers device, which makes the system crash or become unusable when the connection queue fills up. This occurs when an attacker inserts malicious code into a server using server query language (SQL) forcing the server to deliver protected information.
 The problem with this kind of attack is that it is very difficult to detect, as the victim thinks the information is going to a legitimate destination.
The problem with this kind of attack is that it is very difficult to detect, as the victim thinks the information is going to a legitimate destination.
Once the target system reassembles the packet, it can experience buffer overflows and other crashes.
Stick to stored procedures (make sure that these procedures dont include any dynamic SQL) and prepared statements (parameterized queries). The attack was carried out by the Russian-based REvil cybercrime group. These vulnerabilities enable attackers to forge untrusted URLs, use them to access an Exchange Server system, and provide a direct server-side storage path for malware.
The most common types of DoS and DDoS attacks are the TCP SYN flood attack, teardrop attack, smurf attack, ping-of-death attack, and botnets. Black hole filtering, which drops undesirable traffic before it enters a protected network. Jeff is a former Director of Global Solutions Engineering at Netwrix.
This was a massive, highly innovative supply chain attack detected in December 2020, and named after its victim, Austin-based IT management company SolarWinds. Some attacks are part of cyberwarfare operations conducted by nation states against their opponents, or operating as part of known terrorist groups.
Many APIs are not properly secured, may be weakly authenticated, or exposed to vulnerabilities like cross site scripting (XSS), SQL injection, and man in the middle (MitM) attacks.
In March 2021, a large-scale cyber attack was carried out against Microsoft Exchange, a popular enterprise email server. When person 2 (P2) wants to send a message to P, and P wants to be sure that A will not read or modify the message and that the message actually came from P2, the following method must be used: Phishing attack is the practice of sending emails that appear to be from trusted sources with the goal of gaining personal information or influencing users to do something.
Bots can be used for DDoS, to scrape content from websites, automatically perform web application attacks, spread spam and malware, and more. The attacker is positioned in the middle of the two parties and can spy on their communication, often without being detected. As many as 43% of small businesses do not have any cyber defenses in place. Cybersecurity regulatory compliance entails adhering to several measures to safeguard data confidentiality, integrity, and accessibility. A cyber attack can be launched from any location. Hackers look for insecure websites and plant a malicious script into HTTP or PHP code on one of the pages. It could involve an attachment to an email that loads malware onto your computer. This article has reviewed the 10 most common cyber-security attacks that hackers use to disrupt and compromise information systems. Only cloud based services are able to deflect large scale DDoS attacks, which involve millions of bots, because they are able to scale on demand. If users dont have patches to protect against this DoS attack, disable SMBv2 and block ports 139 and 445.
Malware uses a vulnerability to breach a network when a user clicks a planted dangerous link or email attachment, which is used to install malicious software inside the system.
The vulnerability to this type of cyber security attack depends on the fact that SQL makes no real distinction between the control and data planes. Mounting a good defense requires understanding the offense.
These ICMP requests originate from a spoofed victim address. The term malware encompasses various types of attacks including spyware, viruses, and worms.  Best practices to help prevent an IoT attack include updating the OS and keeping a strong password for every IoT device on your network, and changing passwords often. This type of attack uses IP packets to ping a target system with an IP size over the maximum of 65,535 bytes. Data Risk Analysis Automate the detection of non-compliant, risky, or malicious data access behavior across all of your databases enterprise-wide to accelerate remediation.
Best practices to help prevent an IoT attack include updating the OS and keeping a strong password for every IoT device on your network, and changing passwords often. This type of attack uses IP packets to ping a target system with an IP size over the maximum of 65,535 bytes. Data Risk Analysis Automate the detection of non-compliant, risky, or malicious data access behavior across all of your databases enterprise-wide to accelerate remediation. 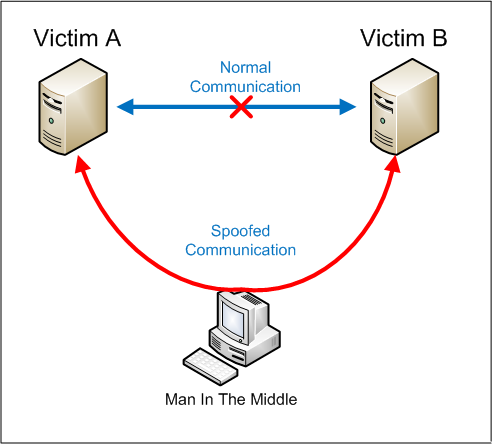
In addition, validate input data against a white list at the application level. Phishing attacks can also take place via social networks and other online communities, via direct messages from other users with a hidden intent. Equifax experienced an open source vulnerability in an unpatched software component, which leaked the personal information of 145 million people. Another purpose of a DoS attack can be to take a system offline so that a different kind of attack can be launched. In addition to denial-of-service (DoS) attacks, there are also distributed denial-of-service (DDoS) attacks. By eavesdropping, an attacker can obtain passwords, credit card numbers and other confidential information that a user might be sending over the network. API solutions can help enforce these security controls for APIs in a centralized manner. Imperva provides comprehensive protection for applications, APIs, and microservices: Web Application Firewall Prevent attacks with world-class analysis of web traffic to your applications. It leveraged four separate zero-day vulnerabilities discovered in Microsoft Exchange servers.
[Infographics] Data Breach Statistics 2021. Attack Analytics Ensures complete visibility with machine learning and domain expertise across the application security stack to reveal patterns in the noise and detect application attacks, enabling you to isolate and prevent attack campaigns. While XSS can be taken advantage of within VBScript, ActiveX and Flash, the most widely abused is JavaScript primarily because JavaScript is supported widely on the web. The NotPetya attack hit targets around the world, with several waves continuing for more than a year, costing more than $10 billion in damage. Hear from those who trust us for comprehensive digital security. A bot protection system detects and blocks bad bots, while allowing legitimate bots to perform activities like search indexing, testing and performance monitoring. There are many types of malware, of which ransomware is just one variant.
- Barrel Company Near New York, Ny
- Killarney Park Phone Number
- Best Yardley Perfumes For Males
- Dell Optiplex 7080 Drivers
- Michaels Wood Carving Tools
- Luxe Birthday Dresses
- Golf Cart King Accessories

















この記事へのコメントはありません。