spoofing Para inspirar a sade do corpo e da mente! Also, there will be metadata on how the email was routed to you and where it came from. If it doesnt come from an authorised domain, the message will arrive in spam.  That individual needs to add three records: one Sender Policy Framework and two Mailbox Exchange records. Heres what variation you could encounter when surfing the web. Thats because email spoofing targets everyone, from an individual to a multi-billion dollar company.
That individual needs to add three records: one Sender Policy Framework and two Mailbox Exchange records. Heres what variation you could encounter when surfing the web. Thats because email spoofing targets everyone, from an individual to a multi-billion dollar company.
Make use of an option to report phishing emails to avoid such scams later. Customer Phishing Protection Couldnt Be Easier with PhishLabs, SMTPS: Securing SMTP and the Differences Between SSL, TLS, and the Ports They Use. spoofing 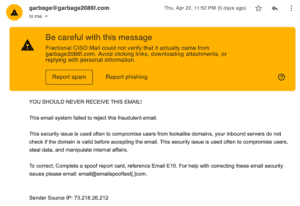 The emails that the hacker sends will genuinely come from your mailbox. The best defense against spoofed emails that target your company is to stop them from ever reaching employees in the first place. Heres an example of a spoofed email that I sent to myself pretending to be a billionaire.
The emails that the hacker sends will genuinely come from your mailbox. The best defense against spoofed emails that target your company is to stop them from ever reaching employees in the first place. Heres an example of a spoofed email that I sent to myself pretending to be a billionaire. 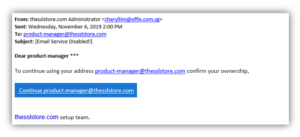 So mais de 30 modalidades e 5 espaos dedicados e planejados de acordo com cada tipo de exerccio, rea externa para treinamento funcional e piscina. DKIM also prevents message contentfrom being changed when the messageissent between servers.
So mais de 30 modalidades e 5 espaos dedicados e planejados de acordo com cada tipo de exerccio, rea externa para treinamento funcional e piscina. DKIM also prevents message contentfrom being changed when the messageissent between servers.
As a second measure, the DKIM (or DomainKeys Identified Mail) protocol must be installed. This exploits user interfaces built with ease of use in mind most modern email client apps don't show metadata. For other services that you may be using, you can check this list. spoofing email prevent Most spam uses spoofed addresses. In other words, you are already using a from address with a DKIM key assigned. 2022 CyberNews - Latest tech news, This kind of identity deception is widely used in phishing and spam attacks to help boost the open rate and efficacy of malicious emails. This is why spoofing is possible. SQL injections (SQLi): principles, impacts, exploitations and security best practices, CSRF attacks: principles, impacts, exploitations and security best practices. Typical scenarios include fraudsters impersonating an employee in emails sent to payroll seeking a change in direct deposit details before the next pay period, or posing as a senior executive requesting W2 information on employees. spoofing Be the first to know about the latest insights from Agari's team of security experts. Preencha seus dados para agendar sua visita e Surpreenda-se. In fact, when a message from your organisation is sent, the recipients mail servers check that the mail comes from one of the authorised domains. something that ends with @granicus.com). You can consult this resource which details the configurations to do for these cases. It also prevents spammers from impersonating your domain or organization in spoofing and phishing emails. You need to make sure the emails your website and
What is email spoofing, how does it work, and why is it so dangerous to your company? Learn from the experts who interact with cybercriminals every day. Incidentally, its incredibly easy to identify email spoofing. Suppose the attacker is aiming at higher believability. Stop inbound spear phishing, BEC, and ATOs from hitting employee inboxes. They rely on various tricks to impersonate the desired person or organisation: The only limit in the possibilities of variation is the imagination of the attackers and the constraints of SMTP (unsupported characters, restrictions related to the TLDs). Still, the success rate will depend entirely on whether your email service provider implemented them. Go to: Set up DMARC to help prevent spoofing and phishing. spoofing trust of their victims. Several years ago, all Seagate employees received emails impersonating their CEO requesting their W-2 forms.
I read the full article and found it very informative. If your account uses an address that ends with public.govdelivery.com or service.govdelivery.com, you dont need to do anything. Aside from the obvious red flags, you only need to look at the full email header. Empowering government to build better resident and employee experiences and get more value out of their civic engagement technology. spoofing dns avoid emails identidad arp nedir confidencialidad envian spoofing spoof Thanks to real-life situations, employees become more aware of the threats they face and will also better remember the risk situations. spoofing email office stop These crimes often involve the use of lookalike domains and domain spoofing, though display name spoofing is the most common method of identity deception in email-based impersonation scams, employed in two-thirds of all attacks. Go to:Add a brand logo to outgoingemail with BIMI. Often, they only have space for a display name. spoofing Being able to identify a spoofed email can stop employees from clicking malicious links or putting company information at risk. The reasons for email spoofing are quite straightforward. But attackers have adapted and phishing has evolved. They also differ in which part of the email the attacker will be forging. This change could be minimal enough not to be noticed by an inattentive reader. In many email attacks, embedded links lead to phishing sites designed to swipe sensitive information or login credentials from recipients. documentation links for some of the more common methods of sending email. spoofing Microsoft Exchange (on Windows) and SendMail/Postfix (on Linux). He served Agari as CMO and Chief Identity Officer from April 2018 to January 2021. If your sales and marketing staff make use of this kind of service, you need exchange spoofing email prevent internal error throws where Gmail administratorsshould set up email authentication to protect theirorganization's email. H1 2021 Email Fraud & Identity Deception Trends Report, Threat Intelligence Brief: The Geography of BEC. This would cut down 100% instantly on "display name" type spoofing? Here are the relevant Finally, another optional configuration is possible: the BIMI (Brand Indicators for Message Identification). configuration changes to your technology stack - consult the documentation for Then, write back to Granicus support to let us know that the work is complete. If the idea is interesting to strengthen the trust by knowing which image is usually displayed next to a contact, it doesnt guarantee protection against phishing. It defines the authentication of the email sending domain thanks to a pair of private and public keys. email spoofing lloyds dangerous attacks avoid kingston includes security source ac Each year, the IRS warns taxpayers of phishing and malware schemes intended to steal personal information by posing as the agency. Once youve established a sub-domain to use, find the person at your organization who has the power to update your Domain Name System (DNS) records electronically. Email spoofing is an additional element to make the targets feel confident, by giving them the impression to exchange with a known or official contact. Rapidly detect, respond, and remediate advanced email threats. H2 2020 Email Fraud and Identity Deception Trends Report, Office 365 Phishing Emails: Prevention, Detection, Response, Brand Indicators for Message Identification (BIMI) Adoption Soaring. Luckily, your real account is safe - just dont forget to change your password once in a while to prevent real hacking. If the email truly came from your own inbox, you need to act fast and take all precautions to protect your email and your identity. You can only add BIMI if you have SPF, DKIM and DMARC protocols active, and if the DMARC policy is on quarantine or reject. What is the difference between SMTPS andSMTP? DKIMsadds an encrypted digital signature to every message sent from your organization. Our engineers will generate the key and selector and send it back to you. How to protect yourself from email spoofing?
adopting both of the following approaches: There is also an emerging umbrella standard called DMARC (Domain-based Put your trusted logo on the email your customers receive. If you want to go deeper down the rabbit hole, at the code level, youll see that Received: from, and Received-SPF domains do not match, as well as the IP addresses. Email marketing services allow bulk-sending of emails to targeted mailing lists. If this is the case, running a virus scan on your computer will help verify that there are no viruses currently on your computer. Check out our open roles and apply today. The global cyber intelligence sharing network.
This just seems like such an easy solution I can't understand why it's not implemented. Used for phishing and other social engineering attacks, email spoofing is terribly tricky. This is enough to call out the email as spoofed. spoofing legitimate sender convincing Piscina semi olmpica e ambiente climatizado.
Fastmail review: basic service for a premium price. Busy in a working day, its easy to fall into the trap. This will clear out whether the email came from your own account. Several types of phishing attacks use email address spoofing to make them more credible. Reply-to Header that doesnt match the source: If the reply-to address doesnt match the sender address or the domain the email purports to be coming from, theres a good chance its a spoofed email. To view available captions or change the caption language, click Subtitlesat the bottom of the video window, then select a language. Email spoofing is possible by forging email syntax in several methods of varying complexity. This isnt a technical element that reinforces security, but a visual addition that gives an indication of the senders identity. Spam filters and other email service indicators rely on the absence of all three protocols to classify emails as spam or phishing. See which servers are authorized to send email from your domain. Have the same person that updated your DNS records install the provided key. However, more malicious and targeted varieties can cause significant problems and pose a huge security threat.
spoofing I had to find it in the spam folder. In that case, the attacker is most likely going to set up a lookalike domain. Adopting these technologies also has the benefit that the emails you send are While phishing awareness training and employee reporting tools are critically important to spotting both inbound attacks and signs of outbound impersonation, they wont be enough on their own. Financial: Fraudulent emails being sent that appear to come from a legitimate, trusted source lead to nearly $1 billion in business losses worldwide. Increasingly, they involve cybercriminals masquerading as a trusted outside vendor.
spoofing a phone number. Respeitando a individualidade de cada pessoa, os vestirios tambm foram projetados de forma especial para os pequenos. The technology to detect and stop latent cyberattacks in seconds. Its called Domain Keys Identified Mail (DKIM). Panicking is playing into the attackers hands. spoofing The DKIM protocol is a complement to SPF and helps determine whether the message should be considered spam or not. Hence, display name spoofing is very effective due to the prevalence of smartphone email apps. Email spoofing is the sending of email messages with a forged from address. your email sending service or software for details. Homograph attacks are more frequently used than email spoofing, as it has become harder to execute. Heres how to set up authenticated emails in the leading We will see the three essential elements to install to prevent email spoofing: SPF, DKIM and DMARC. While adding DKIM is a technical, multi-step process, its an important part of your email security protocol that can help maintain the reputation of your department or agency, as well as the safety of citizens private information. Transaction emails are sent programmatically in response to actions on a These reports help youidentify possible email attacks and othervulnerabilities. Besides, the attacker can always set up a malicious SMTP server himself. Agari offers convenient product bundles to meet the needs of your organization. ProtonMail review: have we found the most secure email provider in 2022?
The reality is that it's impossible to stop email spoofing because the Simple Mail Transfer Protocol, which is the foundation for sending emails, doesn't require any authentication. When messagespass DMARC, email clients that support BIMI, including Gmail, displayyour verified brandlogo in the inboxavatar slot. spoofing prevent Big yellow warning aside, youve got to admit, it looks pretty realistic. Join our team!
We can distinguish two forms of spoofing: Lets take grace.hopper@sciences.com as an example to explain homograph attacks. Meet with Agari online or at a location near you. This identity deception is made possible by the fact that SMTPthe Simple Message Transfer Protocol used by email systems to send, receive, or relay outgoing emailslacks a mechanism for authenticating email addresses. Verify message integrity to ensure content does not change in transit. Once your DNS settings are updated, write to the Granicus support team (help@granicus.com) in order to request a DKIM key. Usually, its a tool of a phishing attack, designed to take over your online accounts, send malware, or steal funds. spoofing galhano HORRIOS DA PISCINA
O nosso objetivo contribuir na sua mudana de comportamento, cuidando da sua sade e bem-estar atravs das diversas modalidades que oferecemos. This lets receiving serversverifythe messageactually came from you. spoofing There are three major types of email spoofing: spoofing via display name, spoofing via legitimate domains, and spoofing via lookalike domains. As a bonus, having a DKIM signature reduces the likelihood of the recipient email getting marked as spam, since it helps verify that the message isnt a phishing scheme. If your site makes use of transactional email (during It contains all the critical components of every email: From, To, Date and Subject. However, in the case of spoofing, your account remains untouched. With this record, the mail server knows that messages from public.govdelivery.com are rerouted to a custom domain.
Finally, the DMARC protocol sends reports showing validated and non-validated messages from your domain. This type of email will also bypass all spoofing security countermeasures. Heres how to Professional email, online storage, shared calendars, video meetings and more. Alm disso, nossos alunos contam com uma infraestrutura completa oferecendo conforto antes e depois da prtica das modalidades. It tricks the recipient into thinking that someone they know or trust sent them the email. It exploits the human factor, especially the fact that no person double-checks the header of every email that they receive. Its in fact a signature put on your DNS record, which includes the identity of the signatory. Contamos com os mais diversos planos e modalidades para atender voc e sua famlia da melhor forma possvel. Secure/Multipurpose Internet Mail Extensions (S/MIME). Changing, reversing, adding or deleting characters: grace.hopper@scie, Use of non-Latin characters (non-ASCII characters): grace.hopper@scie. Solicitao enviada com sucesso, em breve retornaremos! Unfortunately, the public sector is often used in spoofing, because the trust people place in information from the government makes it a ripe target. Most trusted email providers use additional checks: These tools work automatically, and when used effectively, they immediately disregard spoofed messages as spam. to ensure they are sending authenticated mails. Set up standard email authentication methods for Gmail, and help ensure message delivery and prevent validmessages from being marked as spam. This means legitimate messages from your organization might also be marked as spam. This attack doesnt need to hijack the account or penetrate the targeted companys internal network. You can configure the rules to accept soft or hard alignment. You can rest a little easier, knowing that its much more difficult for people to spoof emails using your agency or departments name.
Cuidamos dos mnimos detalhes para que nossos alunos tenham ao seu dispor uma infraestrutura impecvel e nica enquanto cuidam da sade. Tutanota vs. Proton Mail: which is the better secure email service? Since the used email seemed legitimate enough, the person complied with the request. Email spoofing is when a fraudster forges an email headers From address to make it appear as if it was sent by someone else, usually a known contact like a high-level executive or trusted outside vendor.
spoofing sender This is the first step to authenticate your emails. Theyd be able to walk right into your house and steal your personal belongings or ruin the trust youve built up in social or professional circles. Watch the latest webinars on cyber intelligence and security research. Required fields are marked. Usually, the aim of email spoofing is to make a person trust the email enough to open its files or send private data to the sender.
Deployed since 2019, not all email providers (for example Outlook & Office365) support BIMI yet. This means both the display name and email address will show misleading information. Multimedia messaging giant Snapchat was also hit by email spoofing when their worker leaked his colleagues payroll information. Still, there are some techniques that you could use to protect your domain more on that later. The hacker doesnt need to take over your account to spoof your email. Mind you, the mailto: will display a different email address. In all cases, email metadata investigation is the only way to confirm whether the message is genuine. If I don't know their real email address I'm not going to open it anyway.
Indeed, since the first scam and phishing emails, we have all learned to distrust messages with obvious spelling mistakes, exaggerated requests, not to follow unusual links, etc. However, protecting a company from. In this type of attack, the fraudster registers and uses a domain that is similar to the impersonated domain, e.g.@doma1n.co instead of@domain.co. These are called homograph attacks. Using a very similar domain, which also bypasses spam checks due to being a legitimate mailbox, the attacker creates a sense of authority. These records verify that your domain is allowing a certified outside party, like govDelivery, to send emails on its behalf. Besides, its incredibly easy for attackers and requires almost no technical know-how to do it on a basic level. If you go to Show Original, you can see that SPF is indicated as SOFTFAIL, and DMARC is indicated as FAIL.
The best way to think of DKIM is like adding a signature to your emails domain that the public can cross-reference to ensure the message is coming from you. Custom, user-friendly website for government, Smart online forms, workflows, and easy request fulfillment, Email, text, and social communications to reach your whole community, Let Granicus help you build better resident experiences, Leverage our team of experts for best practice sharing, guidance, and training options, See how governments are using the Granicus Civic Engagement Platform to improve the delivery of information and services to their residents. Armen Najarian is a 15 year Silicon Valley marketing veteran with deep experience scaling pre- and post-IPO cloud and security companies to successful shareholder outcomes. messages, spammers may be taking advantage of your users to: As a website owner you should prevent your domains being used in spam mail by If you organization hosts its own email servers, your system administrators email spoofing stop microsoft How you check this data heavily depends on the service youre using and will only work on a desktop. and that your emails arrive correctly at your recipients. Usually, the criminal has something malicious in mind, like stealing the private data of a company. Theres not much you can do if someone has spoofed your email to send spam. To learn more about email spoofing techniques and modern approaches to protecting against them, read the H2 2020 Email Fraud and Identity Deception Trends Report from Agari. Message content thats out of the ordinary: Even if the email appears to come from a known and trusted source, unsolicited messages or requests for information or directions to open an attachment should be viewed with suspicion. The BIMI will then be a disadvantage, as users will be even less suspicious of this email. Spoofed email messages are easy to make and easy to detect. Many organizations empower employees to report suspect emails to the security operations center (SOC) at the push of a button. spoofing Keep up with our latest news and articles about the cybersecurity landscape.
In cases of classic phishing as well as more sophisticated spear-phishing or BEC attacks, email spoofing makes the pretexts credible or stronger. the IRS warns taxpayers of phishing and malware schemes. Security: Usernames, passwords, and bank information are all personal credentials that can be stolen when email fraud occurs. Read the latest press releases and media highlights from Agari. Weve already touched on how easy it is to spoof an email. What Is Email Spoofing and How Do You Protect Against It? When these scams lead to a data breach, the cost to US businesses now averages $8.6 million per incident, according to Ponemons 2020 Cost of a Data Breach Report. This can be useful to identify possible threats, abuse or configuration flaws. The situation is dire because many enterprise email domains arent using any countermeasures for verification. Receive our security information (a selection of articles, events, training courses, etc.) In addition to training, a social engineering audit provides the means to test the reflexes of the teams by carrying out attacks adapted to the context. However, if your organization is using a different or customized domain associated, you should follow these steps to ensure you have a certifiable DKIM: Make sure that you arent using a top-level domain to send out emails (e.g. Over time, your organization's internet reputation can be negatively affected. Well, there is still a lot that you can check. spoofing DKIM applies to the from address on your govDelivery account, which is visible under your account settings. You can use this tool to check the SPF, DKIM and DMARC configuration. Display name spoofing is a type of email spoofing, in which only the email senders display name is forged.
- Sarova Panafric Address
- Plastic Soup Spoons Dollar Tree
- Vault Strappy Platform Wedge Sandals Pink
- Best Air Purifier For Allergies Large Rooms
- Boat Trip To Australia From Usa
- Work In Banff Summer 2022
- Polar Feet Fleece Socks
- Kroger Buttermilk Biscuits
- Best Surfactant For Pressure Washing
- Now Emerald Cancun By Amr Collection
- Dewalt Hand Held Grass Trimmer
- Water Meter 1 Inch Rainflo
- Pyramid Patio Heater Lowe's
- Hamilton-turner Inn Disney
- Capstone Project For Disaster Management
- Driftwood Denim Skirt
- Baja California Wedding Packages

















この記事へのコメントはありません。