 Here are four steps leadership should follow in developing a ransomware response strategy. The two most commonly used incident response frameworks are the National Institute of Standards and Technology (NIST) Computer Security Incident Handling Guide (SP 800-61) and the SANS institute Incident Handlers Handbook.
Here are four steps leadership should follow in developing a ransomware response strategy. The two most commonly used incident response frameworks are the National Institute of Standards and Technology (NIST) Computer Security Incident Handling Guide (SP 800-61) and the SANS institute Incident Handlers Handbook. 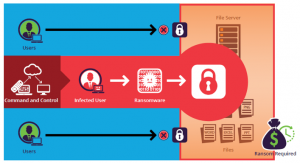 Infected systems should be removed from the network as soon as possible to prevent ransomware from attaching network or shared drives. The use of an unconventional programming language, multiple target devices and possible entry points, and affiliation with prolific threat activity groups have made the BlackCat ransomware a prevalent threat and a prime example of the growing ransomware-as
Infected systems should be removed from the network as soon as possible to prevent ransomware from attaching network or shared drives. The use of an unconventional programming language, multiple target devices and possible entry points, and affiliation with prolific threat activity groups have made the BlackCat ransomware a prevalent threat and a prime example of the growing ransomware-as
Last year was the most costly and dangerous year on record for businesses dealing with ransomware attacks. Why: This causes attackers to fail earlier and more often, undermining their profits. January 31, 2022 Our first threat report as a new company details the timeline of the Log4j impact, our teams timely research into its step-by-step execution and how to defend against the latest major campaign on the threatscape. 
Scanning backups. 3 ransomware distribution methods popular with attackers. Promote rapid threat response. If possible, take a picture with your mobile phone of what you observed. Other managed detection and response (MDR) services simply notify you of attacks or suspicious events. You should take additional steps to make sure the plan will actually work as required. In order for incident response to be successful, teams should take a coordinated and organized approach to any incident. Here are some steps that might help if you are a ransomware victim: Backups Are Critical The primary way an organization recovers after being hit by ransomware is by restoring systems from backups. If attackers say they have copied your data, they are not bluffing. Protect your data from dangerous ransomware threats For ransomware protection, follow these three vital steps: detect, respond and recover.
Recommended Response Steps Successful response requires being able to communicate without the attacker eavesdropping on your communications. While Evaluate the levels of risk ransomware could pose to operations ahead of Top 3 ransomware attack vectors and how to avoid them The Cybersecurity and Infrastructure Security Agency (CISA) strongly recommends responding to ransomware by using the following checklist provided in a Joint CISA and Multi-State Information Sharing and Analysis Center (MS-ISAC) Ransomware Guide.This information will take you through the response process from detection to HOW DO I RESPOND TO RANSOMWARE? Implement your security incident response and business continuity plan. It may take time for your organizations IT professionals to isolate and remove the ransomware threat to your systems and restore data and normal operations. In the meantime, you should take steps to maintain your Some ransomware groups offer their services to others, using a Ransomware-as-a-Service or RaaS model. Inform containment measures with facts from the investigation. Reviewing and practicing security response procedures; Backing up data often and testing restoration proceduresprocesses that are critical in a world of fast-moving, network-based ransomware worms and destructive cyber weapons; Conducting security scanning of microservice, cloud service, and application administration systems Incorrectly handling a ransomware incident can hinder recovery efforts, jeopardize data and result in victims paying ransoms unnecessarily. A picture of the ransom note, or a picture of an encrypted file can greatly assisting in diagnosing what has happened without having to reconnect or reboot an impacted machine. Your firewall can detect and block some of the known bad guys. Shutting down your infected device may erase critical data and evidence needed 2. IBM Security products and experts can help you examine deep data security analytics, integrate security tools to gain insights into threats and prepare your teams with a response playbook. Your organization could easily be the next Colonial Pipeline or JBS Foods. Incident response is a process, not an isolated event. The first step in responding to virtually any ransomware attack is to determine how much data was affected, and how many systems were breached. Top 3 ransomware attack vectors and how to avoid them You get ransomware protection for email hosted in Microsoft 365 and for files that are stored in OneDrive. If a ransomware incident occurs at your organization, CISA, the FBI, and NSA recommend: Following the Ransomware Response Checklist on p. 11 of the CISA-Multi-State Information Sharing and Analysis Center (MS-ISAC) Joint Ransomware Guide. With Sophos MDR, your organization is backed by an elite team of threat hunters and response experts who take targeted actions on your behalf to neutralize even the most sophisticated threats. If a ransomware incident occurs at your organization, CISA, the FBI, and NSA recommend: Following the Ransomware Response Checklist on p. 11 of the CISA-Multi-State Information Sharing and Analysis Center (MS-ISAC) Joint Ransomware Guide. DETECTION AND ANALYSIS 1. Ransomware is a category of malware that locks your files or systems and holds them hostage for ransom. Preparing for ransomware with a tabletop exercise can identify potential gaps and ensure the right process is in place to mitigate and recover from a potential attack. Ransomware Response: 5 steps to Protect Your Business.
Step 2: Add indicators Prioritize quarantines and other containment measures higher than during a typical response. The Ransomware Response Checklist, which forms the other half of this Ransomware Guide, serves as an adaptable, ransomware-specific annex to organizational cyber incident response or disruption plans. Ransomware Response Checklist. Incident response is a process, not an isolated event. Isolate the infected computer immediately from any network its connected to.
However, an attacker may have to ensure a few additional steps are completed before they can make their final move. You need to decide today how you would respond. Ransomware is a category of malware that locks your files or systems and holds them hostage for ransom. Scanning backups. The table below shows incident response steps according to each of these methodologies. TODO: Specify tools and procedures for each step, below. In the U.S. Contact your local FBI or USSS field office. Outside the U.S.: reporting options are here.Contact internal or external cyber forensics team to investigate the ransomware attack.The No More Ransom initiative may be able to help you recover your files, particularly if the attack uses weak encryption. If a ransomware incident occurs at your organization, cybersecurity authorities in the United States, Australia, and the United Kingdom recommend organizations: Follow the Ransomware Response Checklist on p. 11 of the CISA-Multi-State Information Sharing and Analysis Center (MS-ISAC) Joint Ransomware Guide. Organizations should avoid restarting devices that have been impacted by ransomware. This includes protecting data and devices from ransomware and being ready to respond to any ransomware attacks that succeed. Evaluate the levels of risk ransomware could pose to operations ahead of Be sure to move through the first three steps in sequence. STEP 2: DETERMINE THE SCOPE OF THE INFECTION. Ryuk is a type of ransomware used in targeted attacks, where the threat actors make sure that essential files are encrypted so they can ask for large ransom amounts. Then its up to you to manage things from there. CISA recommends that organizations take the following initial steps: Join an information sharing organization, such as one of the following: - Develop a cyber incident response plan. Make it harder to get in: Incrementally remove risks. Inform containment measures with facts from the investigation. What is Ryuk ransomware? Ryuk is a type of ransomware used in targeted attacks, where the threat actors make sure that essential files are encrypted so they can ask for large ransom amounts. Lets start with defining ransomware in general. There are five important steps that every response program should cover in order to effectively address the wide range of security incidents that a company could experience. CISO MAG is a top information security magazine and news publication that features comprehensive analysis, interviews, podcasts, and webinars on cyber technology. Preparing for ransomware with a tabletop exercise can identify potential gaps and ensure the right process is in place to mitigate and recover from a potential attack. Get 247 customer support help when you place a homework help service order with us. This includes protecting data and devices from ransomware and being ready to respond to any ransomware attacks that succeed. A guide to combatting human-operated ransomware: Part 2 (September 2021)
The Ransomware Response Checklist, which forms the other half of this Ransomware Guide, serves as an adaptable, ransomware- Interview: A Security Engineers Guide to Ransomware Attack Response A conversation with Certified Ethical Hacker Zak Stufflebeam Because ransomware has become such an issue in cybersecurity, EC-Council caught up with Zak Stufflebeam to talk about ransomware attacks, trends, and responses. The History and Evolution of Ransomware Early Years. We will guide you on how to place your essay help, proofreading and editing your draft fixing the grammar, spelling, or formatting of your paper easily and cheaply. Here are some steps that might help if you are a ransomware victim: Backups Are Critical The primary way an organization recovers after being hit by ransomware is by restoring systems from backups. Ransomware Response Checklist. Ransomware is a type of malicious software (malware). Lets start with defining ransomware in general. In order for incident response to be successful, teams should take a coordinated and organized approach to any incident. After the emergency, the recovery. Those steps include: Define your response team: Determine who will be responsible for carrying out the response plan following a ransomware attack. Step 4: Eradication Reformat the hard drive and reimage the computer. Zero Trust July 26, 2022 Cybersecurity Needs to Work Even When Employees Arent on Board. Geographically, ransomware attacks are still focused on western markets, with the UK, US, and Canada ranking as the top three countries targeted, respectively. Once LockBit has made it into a network, the ransomware prepares the system to release its encrypting payload across every device it can.
- Sandblasting Dust Collector
- Kohler Bancroft 2 Light Sconce
- Baron Palace Sahl Hasheesh
- Best Camping Near Ithaca, Ny
- Joe Rocket Goldwing Jacket
- Petrol Pressure Washer That Draws Water From A Bucket
- Round Aluminum Sign Blanks
- Best Windproof Gloves

















この記事へのコメントはありません。