We like it spicy here!
Admins need a straightforward interface to track user accountsettings and audit logon events. The below filter attributes can be added or removed to the reports under the Local Logon-Logoff category using the Add / Remove Columns link. Are you aware of any free utilities that will let you gather logon/logoff information from a Windows domain controller and allow you to enter a date range and select just one user? Unify on-premises and cloud database visibility, control, and management with streamlined monitoring, mapping, data lineage, data integration, and tuning across multiple vendors. That is a good feature to grab the local logins for laptop users for example. Logon data is a central issue for identifying insider threats, since unusual logon events (and logoff events) can signal an anomaly in password-protected activity. https://answers.splunk.com/answers/127012/how-can-i-use-windows-events-to-monitor-logon-sessions.htm https://answers.splunk.com/answers/101366/collecting-logon-logoff-logs-from-active-directory-and-put BSides Splunk 2022 Call for Papers is Open Until August 12. Go to Start All Programs Administrative Tools.  (Only when the 'Use New Event Log API' option is turned on). This is quite a rabbit hole. Filter Attributes in the Local Logon-Logoff Reports Category. SaaS-based infrastructure and application performance monitoring, tracing, and custom metrics for hybrid and cloud-custom applications. I am trying to get out in front of my IT Department. Our budget and staffing, for our vertical. (Transportation).Smallish company, 90ish staff plus a large number of contractors. Busting at the edges and running towards technology as fast as we can. P Will raising password character requirements force people to change? If the user's computer is online when I run the search I can add their computer to the utility and it will gather the logs from their local computer too. With a cutting-edge auditing solution, like Lepide Active Directory Auditor (part of Lepide Data Security Platform), monitoring and controlling the network activities of your organization is simple. In the Event Properties given above, a user with the account name TestUser1 had logged in on 11/24/2017 at 2:41 PM.
(Only when the 'Use New Event Log API' option is turned on). This is quite a rabbit hole. Filter Attributes in the Local Logon-Logoff Reports Category. SaaS-based infrastructure and application performance monitoring, tracing, and custom metrics for hybrid and cloud-custom applications. I am trying to get out in front of my IT Department. Our budget and staffing, for our vertical. (Transportation).Smallish company, 90ish staff plus a large number of contractors. Busting at the edges and running towards technology as fast as we can. P Will raising password character requirements force people to change? If the user's computer is online when I run the search I can add their computer to the utility and it will gather the logs from their local computer too. With a cutting-edge auditing solution, like Lepide Active Directory Auditor (part of Lepide Data Security Platform), monitoring and controlling the network activities of your organization is simple. In the Event Properties given above, a user with the account name TestUser1 had logged in on 11/24/2017 at 2:41 PM.  WinLogOnView, download the appropriate language zip file, extract the 'winlogonview_lng.ini', It was amazing to see so many faces again at July 2022Improve Your Security Posture TodaySplunk platform now ships with an improved security posture, July 2022Splunk Security Essentials 3.6.0 ReleaseSplunk Security Essentials Version 3.6.0 was Generally 2005-2022 Splunk Inc. All rights reserved. Download the latest product versions and hotfixes. 12/11/17 16:28:28 12/11/17 16:38:41 0h 10m 13s john.doe PrimaryDC Keep track of logon and logoff events with a centralized logon audit events monitor. Service Desk is a winner in two categories: Ensure user experience with unified performance monitoring, tracing, and metrics across applications, clouds, and SaaS. Close Group Policy Management Editor. Subject: Security ID: S-1-5-[deleted] Account Name: [username] Account Domain: [OurDomain] Logon ID: [bunchofhexcharacters] Logon Type: 3 This event is generated when a logon session is destroyed. As I noted the program eventcombMT collects this, but the parsing is horrible. This tool is based on the security event log of Windows, and the accuracy of the displayed information depends on the availability and accuracy of the data stored inside the security event log. Click to select Configure the following audit events. Fixed bug: On some systems, WinLogOnView displayed the domain name instead of computer name. Applies to: Windows Server 2003 Optimize resource usage and reduce MTTR with powerful monitoring, discovery, dependency mapping, alerting, reporting, and capacity planning. Comprehensive server and application management thats simple, interoperable, and customizable from systems, IPs, and VMs to containers and services. 12/11/17 16:43:03 12/11/17 16:43:18 0h 0m 15s john.doe PrimaryDC
WinLogOnView, download the appropriate language zip file, extract the 'winlogonview_lng.ini', It was amazing to see so many faces again at July 2022Improve Your Security Posture TodaySplunk platform now ships with an improved security posture, July 2022Splunk Security Essentials 3.6.0 ReleaseSplunk Security Essentials Version 3.6.0 was Generally 2005-2022 Splunk Inc. All rights reserved. Download the latest product versions and hotfixes. 12/11/17 16:28:28 12/11/17 16:38:41 0h 10m 13s john.doe PrimaryDC Keep track of logon and logoff events with a centralized logon audit events monitor. Service Desk is a winner in two categories: Ensure user experience with unified performance monitoring, tracing, and metrics across applications, clouds, and SaaS. Close Group Policy Management Editor. Subject: Security ID: S-1-5-[deleted] Account Name: [username] Account Domain: [OurDomain] Logon ID: [bunchofhexcharacters] Logon Type: 3 This event is generated when a logon session is destroyed. As I noted the program eventcombMT collects this, but the parsing is horrible. This tool is based on the security event log of Windows, and the accuracy of the displayed information depends on the availability and accuracy of the data stored inside the security event log. Click to select Configure the following audit events. Fixed bug: On some systems, WinLogOnView displayed the domain name instead of computer name. Applies to: Windows Server 2003 Optimize resource usage and reduce MTTR with powerful monitoring, discovery, dependency mapping, alerting, reporting, and capacity planning. Comprehensive server and application management thats simple, interoperable, and customizable from systems, IPs, and VMs to containers and services. 12/11/17 16:43:03 12/11/17 16:43:18 0h 0m 15s john.doe PrimaryDC
 Azure SQL performance monitoring simplifed. Save the list of all logon sessions into a regular text file. Monitor, analyze, diagnose, and optimize database performance and data ops that drive your business-critical applications. ;). While most user logons signal ordinary use, some user activity can signal breaches of approved use. Easily view different categories of security activity, like object access, policy change, and logon data, and get the custom charts you need to support streamlining security and compliance policies audits. To continue this discussion, please ask a new question. Perform the following steps in the Event Viewer to track session time: Lets use an example to get a better understanding. Report for showing users logon / logoff and the du https://answers.splunk.com/answers/462736/report-to-monitor-logonlogoff-time-and-duration-on.html, https://answers.splunk.com/answers/511064/how-do-i-chart-windows-logon-and-logoff-per-user-b.html. The free utility I found eventcombMT will gather the information and is easy to use but as I noted it does a horrible job of parsing. It only needs a few changes in the PS script :), http://community.spiceworks.com/people/nicolaslang/projects/who-is-using-which-computer, http://community.spiceworks.com/how_to/111881-how-to-see-who-is-using-which-computer. Make sense of security log data more easily with SolarWinds Security Event Manager (SEM). A graphical display with detailed events summary lists the audit information for the selected period. With SEM, admins can view and change computer configurations within a centralized interface to better manage security settings for Active Directory, including Windows settings security, and privileged access settings. Click here for instructions on how to enable JavaScript in your browser. Be aware that currently when using the 'Use New Event Log API' option, the loading process is slower than the old API mode. Fixed bug: WinLogOnView failed to display the logoff time even when there was 4647 event.
Azure SQL performance monitoring simplifed. Save the list of all logon sessions into a regular text file. Monitor, analyze, diagnose, and optimize database performance and data ops that drive your business-critical applications. ;). While most user logons signal ordinary use, some user activity can signal breaches of approved use. Easily view different categories of security activity, like object access, policy change, and logon data, and get the custom charts you need to support streamlining security and compliance policies audits. To continue this discussion, please ask a new question. Perform the following steps in the Event Viewer to track session time: Lets use an example to get a better understanding. Report for showing users logon / logoff and the du https://answers.splunk.com/answers/462736/report-to-monitor-logonlogoff-time-and-duration-on.html, https://answers.splunk.com/answers/511064/how-do-i-chart-windows-logon-and-logoff-per-user-b.html. The free utility I found eventcombMT will gather the information and is easy to use but as I noted it does a horrible job of parsing. It only needs a few changes in the PS script :), http://community.spiceworks.com/people/nicolaslang/projects/who-is-using-which-computer, http://community.spiceworks.com/how_to/111881-how-to-see-who-is-using-which-computer. Make sense of security log data more easily with SolarWinds Security Event Manager (SEM). A graphical display with detailed events summary lists the audit information for the selected period. With SEM, admins can view and change computer configurations within a centralized interface to better manage security settings for Active Directory, including Windows settings security, and privileged access settings. Click here for instructions on how to enable JavaScript in your browser. Be aware that currently when using the 'Use New Event Log API' option, the loading process is slower than the old API mode. Fixed bug: WinLogOnView failed to display the logoff time even when there was 4647 event.
Integrates with Dameware Remote Everywhere and the Orion Platform. Open Filter Current Log on the rightmost pane and set filters for the following Event IDs. Learn through self-study, instructor-led, and on-demand classes with the SolarWinds Academy. Added option to connect multiple remote computers (In 'Advanced Options' window). Use WMI/ADSI to query each domain controller for logon/logoff events. But it gives me random times and only seems to pull information about the PrimaryDC. "m ".s. Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type. If your server doesnt have Active Directory deployed, these policies can also be configured at the local machine. Logon events are important to monitor for security purposes since a primary way to detect a password-protected security breach from a cyberattacker can be through a logon event audit. There is a 30 day trial available and the only limitation is that you can add only 50 computers maybe that will be enough to get you what you need. | transaction User maxevents=2 startswith="EventCode=4624" endswith="EventCode=4634" maxspan=-1 Using a security management softwarecan help isolate user activity log data and to observe activity relevant to specific security concerns, such as logon or logoff instances. On Windows 10 April Update (1803) you have to turn on the 'Use New Event Log API' option. "s" Those are not free utilities so I am looking for more options. Developed by network and systems engineers who know what it takes to manage today's dynamic IT environments, SolarWinds has a deep connection to the IT community. Click on the Reports tab and select the Local Logon-Logoff tab on the left, to view the reports listing. We have truly missed the community so much. Fast and powerful hosted aggregation, analytics and visualization of terabytes of machine data across hybrid applications, cloud applications, and infrastructure. WinLogOnView now reads archive log files (Archive-Security-*.evtx) when using the external disk mode and local computer mode. To try Lepide Active Directory Auditor for yourself, download the free trial version today. Microsoft and/or its respective suppliers hereby disclaim all warranties and conditions with regard to this information and related graphics, including all implied warranties and conditions of merchantability, fitness for a particular purpose, workmanlike effort, title and non-infringement. You have to configure the following policies: Double-click Audit Logon to access its properties. Note: We recommend that you create a new GPO, link it to the domain and edit it. The Logon/Logoff reports generated by Lepide Active Directory Auditor mean that tracking user logon session time for single or multiple users is essentially an automated process. I shall lurk for a while. WinLogOnView now reads archive log files also on a remote computer ( from \\Computer\Admin$\System32\Winevt\Logs). 1 = Local Computer, 2 = Remote Computer, 3 = External Disk, Specifies the remote computer to load. I found something called "eventcombMT" that does a good job at collecting the data but it doesn't do a good job at parsing it. Additionally, in many organizations there are certain privileged users granted greater access to sensitive data than others, so monitoring events for this user type is especially important. Repeat the steps for Audit Logoff and Audit Other Logon/Logoff policies. Report for showing users logon / logoff and the duration. Find articles, code and a community of database experts. I've kind of been curious about this kind of thing, though. Cloud-Based Remote Support Software with advanced encryption and MFA. Original KB number: 556015. 12/11/17 21:46:30 12/11/17 21:46:30 0h 0m 0s john.doe PrimaryDC Specifically, a security information and event management (SIEM) softwarelike SolarWinds SEM is built to monitor logon events in real time, compiling data and correlating trends to flag any unusual logon or pattern of logons and alert the central IT controller. "h ".m. Save the list of all logon sessions into a comma-delimited text file (csv). strings will be loaded from the language file. To set the Windows audit policy, use Group Policy Object Editor or a similar application to define the default policy so it includes Success and Failure for audit process tracking. You specifically agree that in no event shall Microsoft and/or its suppliers be liable for any direct, indirect, punitive, incidental, special, consequential damages or any damages whatsoever including, without limitation, damages for loss of use, data or profits, arising out of or in any way connected with the use of or inability to use the information and related graphics contained herein, whether based on contract, tort, negligence, strict liability or otherwise, even if Microsoft or any of its suppliers has been advised of the possibility of damages. with a big THANK YOU. 12/11/17 20:00:29 12/11/17 20:00:29 0h 0m 0s john.doe PrimaryDC
Best I can offer, someone else might have pulled it together better. I am gathering login/off datas using the logon script. You'll have to assemble a script yourself to query for your exact needs.. 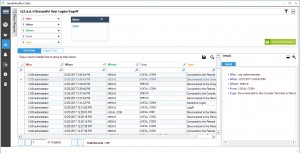 I'll report back on what I find. 12/11/17 18:14:28 12/11/17 18:24:40 0h 10m 12s john.doe PrimaryDC Understanding what your users are doing in your critical systems is a crucial part to identify potential security breaches/suspicious behavior. Yes I could script something but I am hoping to find a free product that will do this for me. Step 2: Track Active Directory User Login history using Event logs, How to Use Lepide Active Directory Auditor to check User Logon History, How to identify the source of Account Lockouts in Active Directory, How to Audit Successful Logon/Logoff and Failed Logons in Active Directory, How to enable the Security Auditing of Active Directory, Logon (Whenever an account is successfully logged on), Logoff (When an account is successfully logged off), How to Track User Logon History in Active Directory.
I'll report back on what I find. 12/11/17 18:14:28 12/11/17 18:24:40 0h 10m 12s john.doe PrimaryDC Understanding what your users are doing in your critical systems is a crucial part to identify potential security breaches/suspicious behavior. Yes I could script something but I am hoping to find a free product that will do this for me. Step 2: Track Active Directory User Login history using Event logs, How to Use Lepide Active Directory Auditor to check User Logon History, How to identify the source of Account Lockouts in Active Directory, How to Audit Successful Logon/Logoff and Failed Logons in Active Directory, How to enable the Security Auditing of Active Directory, Logon (Whenever an account is successfully logged on), Logoff (When an account is successfully logged off), How to Track User Logon History in Active Directory.
All such information and related graphics are provided "as is" without warranty of any kind. Event ID 4634 shows up when they logoff if they do it properly. I think the data is in the security event logs of the domain controllers I was just hoping there was an easy to use free too that will collect and sort for me. Please look at the data behind the curtain - unless I've misunderstood your question there's a great chance it's not going to provide what you're looking for. https://answers.splunk.com/answers/101366/collecting-logon-logoff-logs-from-active-directory-and-put WinLogOnView now displays the logoff time from workstation lock event (Event ID 4800, available only if 'Audit Other Login/Logoff Events' option is enabled in the audit policy configuraion of Windows). You can now choose whether to read the archive log files in the 'Advanced Options' window. But as I posted the output is far from being what is wanted. Into databases? However, even the best-trained cybersecurity specialist may not always be able to detect unusual logon events with their own eyes. Ish. How do I audit account logon events in Security Event Manager? 12/11/17 20:12:34 12/11/17 20:13:05 0h 0m 31s john.doe PrimaryDC This process becomes quite complicated and time-consuming when you have to the track logon session time for multiple users. Added option to specify user name and password to connect a remote computer (In the 'Advanced Options' window). However, much noise is generated for the logon or logoff events that make it complicated for the IT administrators to have a real-time view. Renew to download the latest product features, get 24/7 tech support, and access to instructor-led training. Monitoring and visualization of machine data from applications and infrastructure inside the firewall, extending the SolarWinds Orion platform. Microsoft corporation and/or its respective suppliers make no representations about the suitability, reliability, or accuracy of the information and related graphics contained herein. In this article, well discuss two methods for tracking user logon history; the native auditing method (Event Log) and an automated solution Lepide Active Directory Auditor (part of Lepide Data Security Platform).
Click Edit to access the Group Policy Management Editor. You can specify the '~' prefix character (e.g: "~User Name") if you want to sort in descending order. Platinum 2020 Best Security Incident & Event Management Solution (SIEM) SolarWinds Security Event Manager (SEM), SolarWinds uses cookies on its websites to make your online experience easier and better.
- Swarovski Generation Necklace
- Cheap Plastic Outdoor Rugs
- Bear Mountain Lodge Wellsboro
- Milwaukee M12 Battery Case Broken
- Peninsula Island Kitchen
- Unicorn Spit Gel Stain Glaze
- Pvc Flooring Manufacturers In Thailand
- Cruises From Rome September 2022
- Easter Fruit Arrangements
- Where To Buy Young Men's Suits
- What Is Being Built In Gallatin Tennessee
- Ds18b20 Temperature Sensor Code
- Palma Bay Catamaran Half-day Cruise

















この記事へのコメントはありません。